In this digital era, the analogy of cybersecurity as a defensive structure is more relevant than ever. For a long time, many individuals and organizations relied on just one very strong gate: their antivirus software. This digital gatekeeper’s job is to identify and block known malicious actors, such as viruses, trojans, and worms, which were the primary threats in the past.
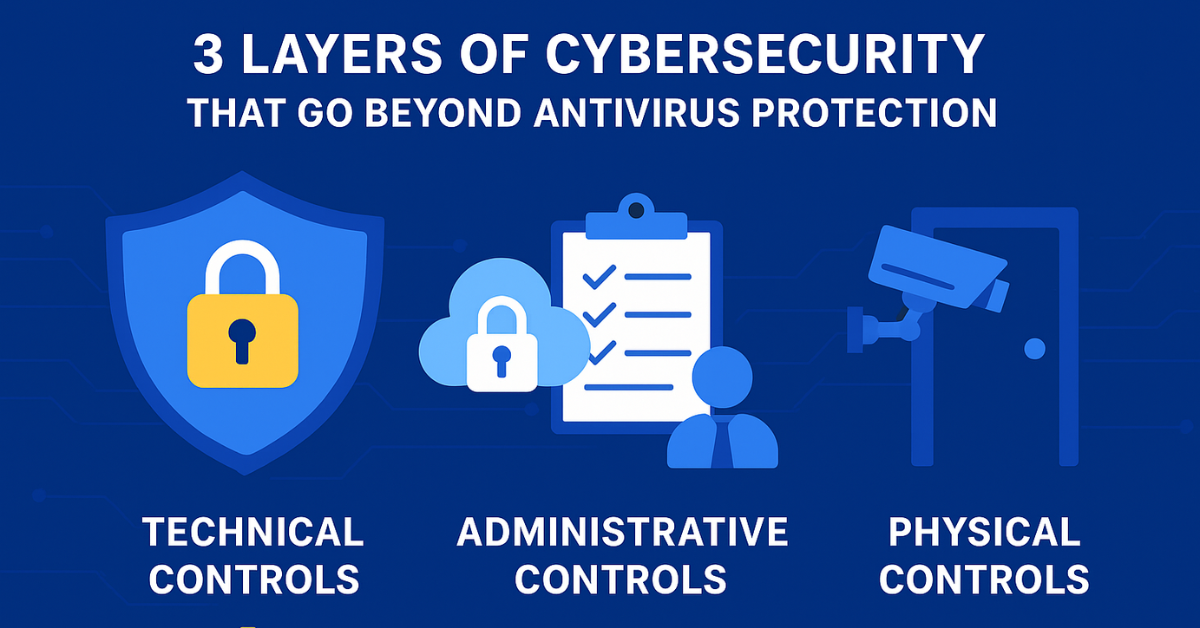
An effective cybersecurity strategy must stand on the concept of a single perimeter. Instead, it must adopt a defense-in-depth approach, creating multiple, overlapping layers of security that protect assets if any layer is compromised. This approach integrates three distinct yet interconnected categories of control: Technical, Administrative, and Physical. These three layers work together to form a comprehensive system that protects both the data and the people, processes, and infrastructure that interact with it.
Layer 1: Technical Controls
In cases where people think of cybersecurity, they usually think of the physical, technology-based protections that are used to keep things safe. These are the hardware and software solutions that are meant to keep systems, networks, and data safe from. Antivirus software is a part of this layer, but it’s only one soldier in a bigger army.
Firewalls and Intrusion Prevention/Detection Systems (IPS/IDS):
A firewall is like the smart, strong main gate of your organization. It does not just stand there. It actively inspects every piece of data (network packet) that tries to enter or leave your trusted internal network. And it blocks unauthorized communication from the untrusted wilds of the internet by filtering traffic based on IP addresses, ports, and protocols using a set of security rules that have already been set.
Intrusion Detection and Prevention systems are the guards who always watch over the business walls. An IDS is the watchman who raises the alarm upon spotting suspicious activity, e.g., an attacker probing for weakness or the patterns of a known cyberattack. An IPS is an elite guard empowered not just to sound the alarm. It actively blocks the attack in real-time, serving the malicious connection before it can cause harm. They work together and provide a critical layer of network traffic analysis that goes far beyond simple port blocking.
Multi-Factor Authentication (MFA):
Passwords alone are a weak key that is easily copied, stolen, or guessed. MFA makes access more secure by requiring users to prove their identity in two or more different ways, usually from these groups:
- Something you know: A password or PIN.
- Something you have: A smartphone with an authentication app, a security token, or a smart card.
- Something you are: A biometric identifier like a fingerprint or facial recognition.
A hacker can’t get into an employee’s account even if they steal their password through a phishing scheme. They need to have the user’s phone or fingerprint to do that. MFA is one of the best and easiest technical controls available today, and it greatly lowers the risk of someone taking over your account.
Data Encryption
Encryption is the art of rendering data unreadable to anyone without the authorization key. It is a conclusive safety net, protecting data’s confidentiality even If all other defenses fail. This control is applicable in two critical states:
- Encryption in Transit: This keeps information safe as it travels over networks, like when you send an email or do online banking. HTTPS and TLS are examples of protocols that make a secure tunnel. So, that anyone who tries to read the communication sees only gibberish.
- Encryption at Rest: This keeps data safe while it is on a device, like a laptop, smartphone, or server in a data center. Full-disk encryption keeps the data on a device’s hard drive safe from thieves if the device is lost or stolen.
With the implementation of robust encryption, an organization ensures that a breached database or a lost laptop becomes a frustrating dead end for an attacker.
By implementing robust encryption, an organization ensures that a breached database or a lost laptop becomes a frustrating dead end for an attacker, rather than a catastrophic data leak.
Layer 2: Administrative Controls
Let’s be real, if technical controls are fortification, administration controls are the laws, training, and governance that guide the occupant. This layer addresses the most unpredictable and often most exploited elements in any security system or human behavior. It is estimated that over 80 percent of successful breaches involve a human element, which makes these policies and procedures not just important but foundational.
Security Awareness Training
Obviously, technology can block many cyberattacks, but it cannot stop an employee from being tricked. The goal of security awareness training is to convert the workforce from a weakest link into a powerful collective human firewall. An effective and informative training is not an annual checkbox exercise but an ongoing, engaging process that includes:
- Phishing Simulations: Sending safe, fake phishing emails to employees regularly to teach them how to spot red flags like strange sender addresses, urgent language, and fake links.
- Social Engineering Education: Informing employees about techniques other than email, like vishing (voice phishing) and pretexting, in which attackers trick them into breaking security rules.
- Clear Reporting Channels: Making it easy for employees to report strange emails or activity without fear of being blamed, so that every user becomes a proactive security sensor.
Access Control Policies (Principle of Least Privilege):
The Principle of Least Privilege (PoLP) is a key part of managing safe access. It says that any user, system, or process should only be given the minimum amount of access—or permissions—needed to do its job. The marketing intern doesn’t need administrative rights to their laptop, and the junior accountant doesn’t need access to the R&D server.
Applying formal policies to enforce PoLP makes the damage from a breach less severe. If an attacker takes over an employee’s credentials, they can only get to what that employee can get to. This containment is very important to stop a small problem from turning into a full-blown data breach or a ransomware attack that affects the whole system.
Incident Response Planning:
There is no way to get through a defense. So, a well-documented, tested, and understood Incident Response (IR) Plan is an important part of good management. When there is a security breach, the organization follows this plan. A strong IR plan, which usually follows the NIST framework (Preparation, Detection & Analysis, Containment, Eradication & Recovery, Post-Incident Activity), makes sure that:
- Roles are clear: Everyone knows their responsibilities during a crisis.
- Communication is swift: Stakeholders, including management, legal, and PR, are informed promptly.
- Damage is minimized: Steps are taken to isolate affected systems and prevent the attack from spreading.
- Recovery is efficient: Systems are restored from clean backups with confidence.
- Learning is captured: The incident is analyzed to improve defenses and prevent a recurrence.
Layer 3: Physical Controls
In this digital age, it’s easy to forget that data and systems are kept in a real place. Physical controls that protect the servers, workstations, and network hardware from real-world threats. If physical security is broken, all the other layers are useless.
Access Restrictions:
At this point, the most basic physical control is being able to keep people from getting into sensitive areas. This includes implementation of security measures that are far more sophisticated than a simple lock and keys:
- Badge Access Systems
- Biometric Scanners
- Security Personnel and Surveillance
Environmental Safeguards:
Hackers aren’t the only thing that can hurt a server room. Environmental threats can lead to huge amounts of lost data and downtime. Some important safety measures are:
- Uninterruptible Power Supplies (UPS) and Generators: They protect against power surges, brownouts, and blackouts. It allows for a graceful system that shuts down or continues operation.
- Climate Control and Air Filtration: It maintains optimal temperature and humidity levels to prevent hardware from overheating and failing.
- Fire Suppression Systems: It installs specialized systems that use inert gases or chemicals to put out fires without hurting delicate electronic equipment, which is different from regular water sprinklers.
Asset Management:
This control involves tracking, securing, and eventual disposal of physical devices. A stolen laptop is not just a financial loss; it is a potential data breach. Effective asset management includes:
- Physical Asset Tagging and Inventory: It keeps a precise record of all company-owned devices.
- Cable Locks and Secure Storage: It uses Kensington locks for laptops and securing devices in locked cabinets when not in use, especially in public-facing offices.
- Strict Disposal Procedures: In terms of destroying or securely wiping old hard drives, smartphones, and USBs to make sure that data can’t be recovered from them after they are thrown away.
Conclusion
The era of relying solely on a single antivirus solution as a primary defense is over. The volume of modern cyber threats demands a more holistic layered strategy. Additionally, by systematically implementing and integrating technical, Administrative, and Physical controls. And medical practices can move beyond a reactive posture and build a proactive, resilient security culture.
This defense-in-depth model acknowledges that security is not just a technological problem, but also a human and physical one. It makes sure that when an attacker gets past one defense (not if), they are immediately met with another, and another, and so on, until their attack is stopped. In the never-ending fight for digital safety, building this multi-layered fortress is not a choice. It is the most important thing you need to do to stay safe and succeed.